A gang called Mustang Panda that the U.S. Department of Justice says is sponsored by the People’s Republic of China has been identified as the hacker group responsible for a recent phishing campaign targeting the U.S. government. The Swiss cybersecurity outfit Acronis sounded the alert (South China Morning Post, January 16, 2026).
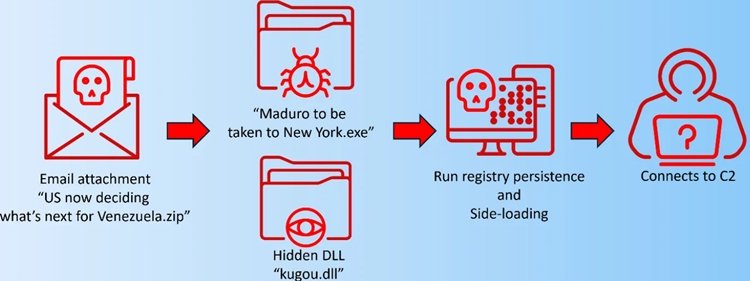
A malware campaign has used recent developments between the US and Venezuela as “thematic lures” to attack US government and policy-related entities with a back door that has espionage-focused capabilities, including basic remote tasking and data exfiltration, Acronis said in a report on Thursday.
The firm said that it attributed this activity to a group named Mustang Panda “with moderate confidence” based on certain infrastructural and operational patterns.
While Acronis did not identify Mustang Panda as a Chinese group, global cybersecurity research teams have described it as a China-based cyber threat actor.
It has been active since 2012 and has launched cyberattacks against organisations worldwide deemed adversaries of the Communist Party, according to Singapore-based cybersecurity firm Cyfirma.
China says that China had nothing to do with this latest Chinese cyberattack. Spokesman: “China firmly opposes the dissemination of false information about so-called ‘Chinese cyber threats’ for political purposes.” But China is not in favor of dissemination of true information about Chinese cyber threats either.
Acronis doesn’t know how much havoc the Mustang Panda manage to wreak. “Unless the attackers were to disclose it, there’s no way to determine how successful the campaign was.” So either a lot or a little data was sucked out of U.S. government servers by the attacks. Some indeterminate number of back doors have been installed and are still in place, or not.
The Acronis site has technical details about the attack. Acronis calls the back door that Mustang Panda is trying to install LOTUSLITE.
Also see:
Acronis: “LOTUSLITE: Targeted espionage leveraging geopolitical themes”











